Equifax Data Breach
Introduction
In September 2017, Equifax was found to be a victim of a cyber-attack that led to the exposure of 143 million people. This attack was among the most severe data breaches to ever occur. The Personally Identifiable Information (PII) stolen by hackers included names, addresses, Social Security numbers (SSN), phone numbers, email addresses, gender, Tax IDs, and birth dates. They also managed to get away with credit card and driver’s license numbers for some of them.
Background
Equifax is one of the largest credit agencies that helps other businesses make informed business decisions. Apart from this, Equifax also sells credit and fraud monitoring and prevention services to their clients. The company’s line of business makes it a natural target for attackers due to the nature of data they possess.
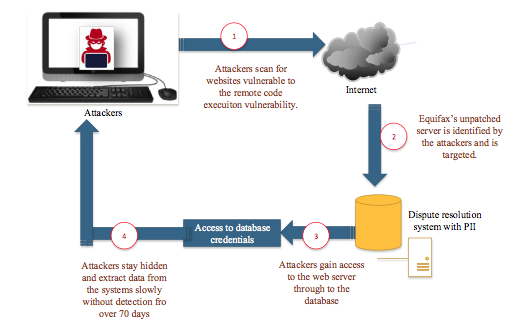
The Vulnerability
To support its business processes, Equifax has employed Apache Struts, an open source web application framework that is used to develop Java EE web applications. Apache Struts is used by Equifax on their dispute resolution web application. In March 2017, Apache foundation discovered a remote code execution vulnerability that allowed attackers to run arbitrary code remotely. This vulnerability ultimately grants access to the web application server without necessary authentication. Over time, Apache released information about the vulnerability as well as offer the necessary patch to fix the issue and prevent exploitation.
What went wrong?
It was discovered that the attack was executed two months after Apache announced the vulnerability and provided patches for it. This implies that Equifax simply delayed or ignored the installation of the update, which led to it being exploited, since the information had been publicly released. By not applying the hot fix on time, Equifax left a window for the attackers to exploit, leading to the data breach.
The breach was not the biggest mistake that happened. The issue was in how Equifax handled the attack, which made people believe that the company was aware of the breach long before they decided to announce it.
As shown by the timeline of event above, Equifax notified its clients of the data breach over two months after the data breach was realized.
From the anatomy above, it is clear that Equifax could have handled this situation better to either stop the breach from occurring or by stopping it before it spread even further.
Guidelines to prevent such a breach
- Adopt a patch management program: It is paramount for organizations to have a robust vulnerability and patch management program that ensures all systems are patched in a timely manner. Majority of the weaknesses that are exploited, including zero-day attacks, are almost always due to missing patches.
- Data classification: For any organization that handles sensitive data, data classification is important. Data can be categorized as public, private, sensitive or confidential. These data labels affect how each category of data is accessed, stored, transmitted or printed. This ensures that sensitive data is accessible only to authorized parties.
- Dual authentication: For infrastructure that holds critical infrastructure, ensure that there is a second layer of authentication besides a user name and password that can be implemented to ensure that only the authorized users have access.