Penetration Testing
Introduction
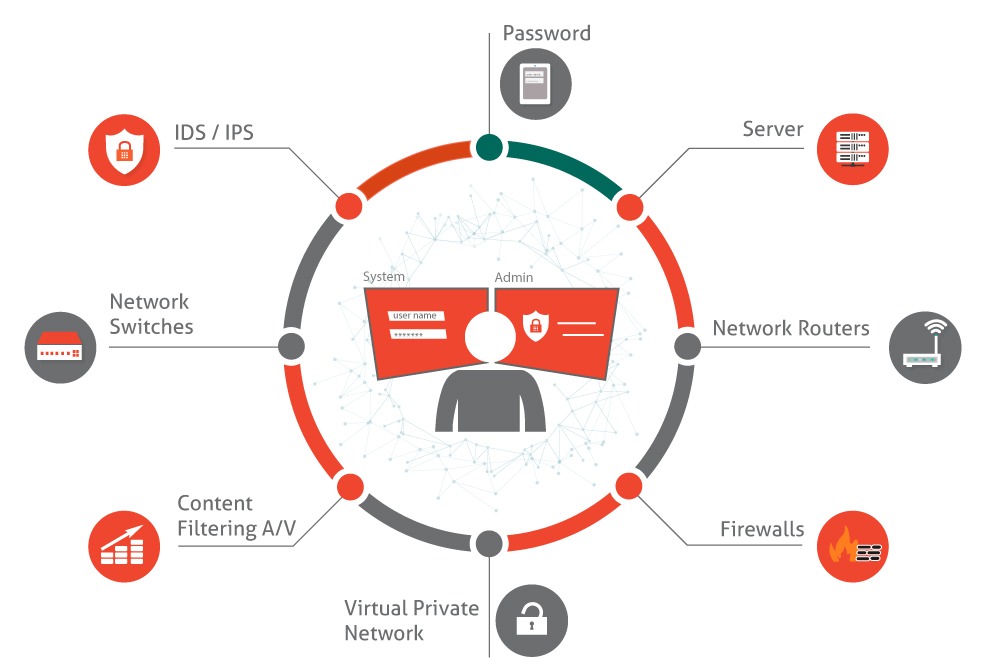
Pen testing is in an authorized cyber-attack in a simulated environment on a computer system in order to determine the security level of the system. Every company needs to conduct a pen test on their network in order to identify vulnerabilities. In this section, I will outline the stages of executing a penetration test.
Stages in penetration testing
- Planning reconnaissance
This is the first stage and involves defining the goals and scope of the testing process. It specifies the system to be tested and the methods to be applied. All intelligence is also gathered in this stage in order to better understand how the target network works and assists in identifying vulnerabilities.
- Scanning
This step involves understanding how the target network and applications held in it will respond to the attempts to intrude it. Static analysis is done to inspect the code of the applications residing on the network and as a result help in estimating the extent of the response. Dynamic analysis involves investigating the code of the application in the running state.
- Gaining access/intrusion
This is the actual attack of the web application. The main activities involved in the intrusion process include SQL injection, backdoors and cross-site scripting. These help in exposing the vulnerabilities in the target to identify exploits in them. The exploitation can be done through escalation of privileges, interception of traffic, and theft of information. An example of a penetration appliance is a code used to hack the system or SQL injector.
- Maintaining access
This is an attempt to determine if the exploit can be maintained without being detected. The use of this tells if the actor can gain further access into the network, if such access exists we can then determine the estimated damage. This stage helps in maintaining persistence on the target system in order to steal new data from the network.
- Analysis
This is the last stage of the test where all the results are compiled together in form of a report. It gives details of the vulnerabilities, the amount of time the attack remains undetected, and the amount of sensitive data accessed. From here the tester will give a recommendation to the business on what needs to be improved on the target network.